How To Prevent a CSRF Attack on a WordPress Website?
Table of Contents
WordPress websites become exposed to CSRF attacks because plugins have vulnerabilities that allow it to happen.
According to a full disclosure report by PluginVulnerabilities.com, many of the popular plugins they checked had security issues that made websites vulnerable to CSRF attacks. To prevent CSRF hacks, developers of plugins need to implement certain security measures. We’ll touch upon these measures briefly and then tell you what you, as a WordPress site owner, can do to stop CSRF attacks.
i. CSRF Preventive Measures for Plugin Developers
If you are a plugin developer, here are a few measures you can take to help prevent CSRF attacks:
1. Anti-CSRF Tokens
An anti-CSRF token is a hidden value that is sent with the particular user’s cookies and request. This is how it works:
- The web server generates this token and is placed as a hidden field on the form.
- When the user fills and submits the form, the token is included in the POST request.
- The server will compare the token generated and the token sent by the user.
If it matches, the request will be valid. If it doesn’t match, the request is deemed invalid. This prevents CSRF attacks from taking place.
A developer can add these tokens while creating or updating their plugin.
2. Using Nonces
Although used interchangeably, Anti-CSRF Tokens and Nonces are different. A nonce value (numbers used once) is like a one-time password that is generated for the request.
When an HTTP request is submitted, the nonce is generated to verify the request. But once used, the nonce is invalidated and the user cannot submit the form again using the same nonce value.
3. Same-Site Cookies
CSRF attacks are possible because of cross-site requests made using the same cookies. A same-site cookie means a cookie can be sent only if the request is made from the same website the cookie was created.
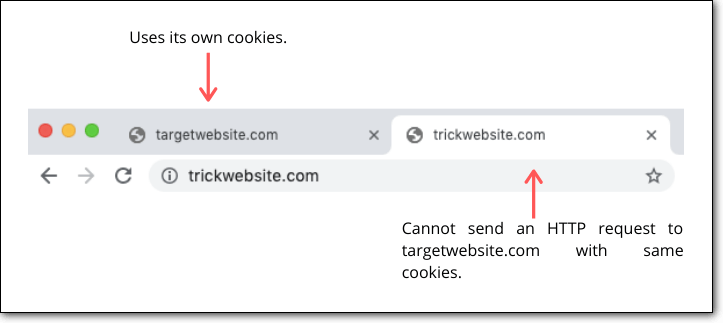
The problem with this method is that expect Chrome and Firefox and a few other browsers, not all browsers support same-site cookies.
This can be used as an additional defense layer but shouldn’t be used alone to prevent CSRF attacks.
We won’t go into further details of these preventive measures because almost all of them can be bypassed by hackers nowadays. Hackers are only getting smart by the day and developing new techniques to overcome the preventive measures we take.
We’ll move on to what proactive and reactive measures you can take as a WordPress site owner to protect yourself against these CSRF attacks.
ii. CSRF Preventive Measures For WordPress Site Owners
As we mentioned above, creators of plugins should take measures to make their application safe. But what if they don’t? How do you know which plugins have implemented anti-CSRF measures?
WordPress rarely stands on its own. Plugins play an important role in the functionality and design of a website. So while WordPress sites need plugins, do you just blindly trust that these plugins have taken appropriate security measures?
No! Website owners need to be on guard and take their own security measures even if plugin developers don’t.
Here’s what you can do to protect yourself from CSRF attacks:
1. Use Anti-CSRF Plugins
There aren’t many plugins available in the WordPress repository that are dedicated to CSRF attacks. Here are two that we found:
(A) Comment Form CSRF Protection – This WordPress plugin adds an anti-CSRF token to your comment forms. The token has a unique value that is kept secret and is impractical to guess. So if a user submits a form, the secret token will be submitted along with it. Only if it matches, the form submission request will be accepted.
(B) Same-site cookies – This plugin works on supported browsers that include Chrome, Firefox, IE and Edge. It ensures that when HTTP requests are submitted, the cookies that are sent are from the same site. This blocks any cross-site requests and therefore, blocks all CSRF attacks.
2. Install an All-round WordPress Security Plugin
There are plenty of security plugins available for WordPress websites. These plugins can keep your site safe from all kinds of hackers including the CSRF kind. But not all security plugins provide you with the same level of security.
Plus, the CSRF attack is tricky to find. Hackers disguise it well from the site owner and the user, so it goes unnoticed. You need a plugin that will be able to detect such disguised malware.
While choosing a security plugin, you need to ensure it does the following in order to stay protected against CSRF attacks:
- Regularly scans your website for any malicious scripts.
- Combs through all files and databases of your website.
- Has the ability to spot any kind of malware – including new, hidden or disguised. (Some plugins only search for already-discovered malware.)
- Alerts you if there is any suspicious activity on your website.
- Gives you an independent dashboard so that you can clean up your website even if a hacker locks you out of your own admin account.
A plugin that gives you such protection and features is MalCare. Once you install the plugin on your WordPress website, it will enable you to get rid of any CSRF attack. It will also get rid of WordPress malware a hacker might’ve added to your site during the hack.
Your website will be protected with a proactive firewall that will block malicious IP addresses and bad bots from visiting your website.
If a hacker manages to hack your site using a malicious cross-site request, this WordPress security plugin will alert you immediately. You can then take action immediately using the same plugin.
3. Harden Your Website
WordPress recommends that you take certain measures to harden your website. This will make it extremely difficult for hackers to break in. We’ve covered a few measures in brief but we recommend reading our extensive guide of WordPress Hardening.
As many of these points are a bit technical, the detailed guide will help you get a better understanding of it. Here are a few hardening measures to prevent or reduce the damage caused by CSRF attacks include:
a. Use Two-Factor Authentication
Having two-factor authentication adds an extra layer of verification of users. A user will have to enter their login credentials, after which a second password will be required. This could be a one-time password sent to the registered email or phone number of the user. It could also be an authentication number generated by an app like Google Authenticator.
b. Block PHP Execution in Untrusted Folders
If a CSRF attack enables a hacker to get access to the files of your website, they can execute PHP functions to perform malicious tasks. (PHP function is a block of code written in a program). You can also disable the PHP executions in places where it doesn’t need to happen.
c. Disable File Editor
If a hacker gets access to your WordPress Administrator account, they can take full control of your website. On the dashboard, they can access “Editor” under your plugins or themes. Here, they can edit or upload their own scripts to display their content, deface your site, SEO spam your users, etc.
d. Change Security Keys
You might’ve noticed you don’t have to enter your login credentials every single time you want to access your WordPress account. It’s already populated in the designated fields. To ensure this information is safe from hackers, WordPress uses security keys that encrypts and stores this data.If a hacker breaks into your site using a CSRF attack, they might get access to this information. They can then change it to something else and use it to keep logging into the admin account of your website when they want.
- You can apply these hardening measures manually as explained in the guide we recommended. Or you can use MalCare to implement them in just a few clicks.

4. Delete All Unused Themes & Plugins
The more plugins and themes you have installed on your website, the more opportunities the hackers have to exploit. It’s best to delete any unused plugins and themes and keep only the ones you use.
Besides these, you can also take a few more security measures like moving your site from HTTP to HTTPS, installing a security plugin, and protecting the login page.
Final Thoughts
CSRF attacks have serious repercussions for both the user and the website.
If a hacker is successful in running their scripts through the HTTP request, they can take over your website. After this, there’s no telling what they can do. They could deface your website to display their own propaganda or sell illegal products or drugs. They could also redirect your website’s visitors to their own websites.






